A blessedly quick objective this one! Quite why the ESXi Configuration Guide is listed in the blueprint is anyone’s idea as ESXi doesn’t contain a firewall! The blueprint also lists vicfg-firewall which is a typo – they mean esxcfg-firewall, as vicfg-firewall doesn’t exist!
Knowledge
- Identify vicfg-firewall commands
- Explain the three firewall security levels
- Identify ESX firewall architecture with/without vCenter Server
Skills and Abilities
- Enable/Disable pre?configured services
- Configure service behavior automation
- Open/Close ports in the firewall
- Create a custom service
- Set firewall security level
Firewall architecture
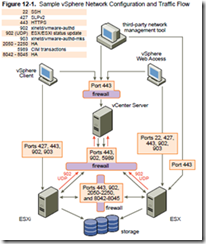
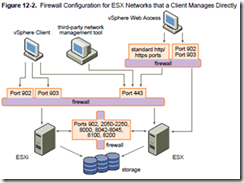
The ESX Configuration Guide talks very generally about where to put firewalls to protect traffic. In reality I can’t see much difference in architecture whether you have a vCenter server or not. These two diagrams are from the ESX Configuration Guide – minimal differences!
The firewall is ESX only (there’s no ESXi firewall as no service console).
Firewall security levels
Three firewall security levels (high is default);
- High (outbound blocked, limited inbound allowed (902, 443,22,123 and a few other including ICMP).
- Medium (outbound allowed, inbound blocked apart from allowed services)
- Off
Firewall Services
A service is a pre-defined set of ports used to enable common functionality. This includes;
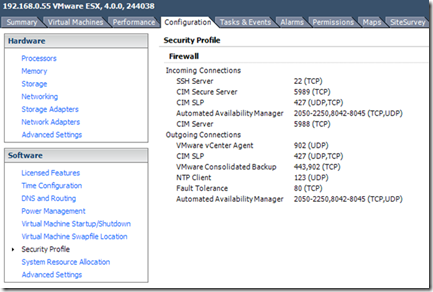
The default services for an ESX host (in an HA cluster) are shown below;
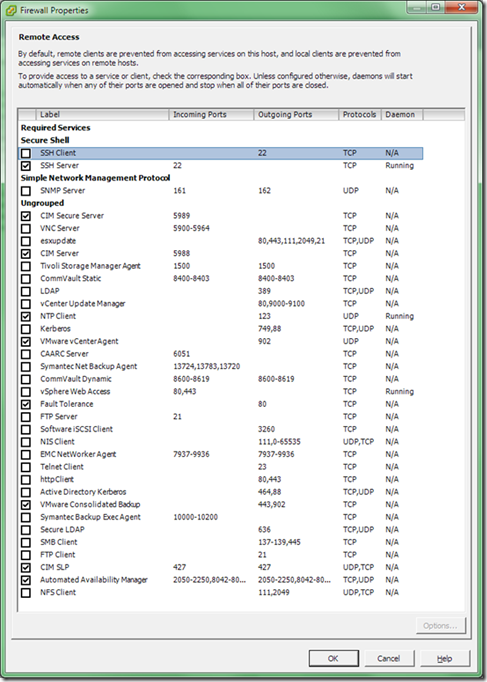
A list of all predefined services is shown below along with the associated ports and protocols;
Service behaviour automation
From the Configuration Guide, “ESX can automate whether services start based on the status of firewall ports”. This can be edited from the Options button for a particular service (under Configuration -> Security Profile). There are three options;
- Start/stop when ports are open/closed. This is the default and recommended option.
- Start/stop with the host.
- Start/stop manually.
One example where you may need to do this is the DCUI service, part of ESXi’s lockdown feature in vSphere 4.1. See section 7.1 for details.
Create a custom service
If you have a management service, device or service which isn’t already in the predefined list it’s possible to create your own. You need to;
- Create an .XML definition file and store it in the /etc/vmware/firewall folder. The easiest method is to copy of the existing .XML files and amend it rather than creating a new file from scratch.
- Enable the new service (esxcfg-firewall -e <your service>)
- Restart the hostd agent (service mgmt-vmware restart).
For details of the .XML file format see Duncan Epping’s blogpost from 2007 which is still relevant and works just fine for vSphere. This also allows you to delegate the administration to a GUI user rather than requiring them to manually open ports by command line (which can be tiresome if it’s a large range for example).
Managing the firewall at the command line (esxcfg-firewall)
While the GUI is pretty simple to use there are occasions when it doesn’t http://premier-pharmacy.com/product-category/antidepressants/ offer enough flexibility. If you need to open ports not in the predefined list (but don’t want to go to the trouble of defining a service as it’s a temporary change) or you need to troubleshoot, the command line’s what you need. NOTE: esxcfg-firewall is ONLY available on the ESX host itself, not via the RCLI (or vMA therefore). There is no vicfg-firewall.
Set the firewall security level to high;
esxcfg-firewall –-blockIncoming --blockOutgoing
Set the firewall security level to medium;
esxcfg-firewall –-allowIncoming --blockOutgoing
Set allow all traffic through the firewall (see VMwareKB1003634);
esxcfg-firewall –-allowIncoming --allowOutgoing
Open/Close ports. You’ll need to do this if you want to allow access to a service, device, or management agent which is not in the pre-defined services previously listed;
# To open a port esxcfg-firewall –o <ports>,<protocol>,<in|out>, <name> # For example esxcfg-firewall -o 873,tcp,in,"rsync" # To close a port esxcfg-firewall –c <ports>,<protocol>,<in|out> # for example esxcfg-firewall -c 873,tcp,in
To restart the firewall;
esxcfg-firewall –r
Show all predefined services;
esxcfg-firewall –s (or esxcfg-firewall –-services)
Enable/disable pre-configured services (SSH etc)
# To enable a predefined service esxcfg-firewall –e <service> esxcfg-firewall -e sshClient # To disable a predefined service esxcfg-firewall –d <service> esxcfg-firewall -d sshClient
To query the existing rules;
esxcfg-firewall -q
Below is a screenshot of querying the default firewall rules for a host in an HA/DRS enabled cluster. I’ve highlighted in red where the HA ports are shown, along with the firewall security level (high) and enabled services summary (towards the bottom).
The ESX firewall uses a modified IP Tables, the default firewall shipped with Red Hat Enterprise Linux v5. If you want to know more about how it works under the hood here’s a good tutorial. All esxcfg-firwall does is call iptables under the hood – if you scan the firewall logfile you’ll see multiple calls to iptables.
NOTE: Even though you can modify the firewall by using ‘iptables’ (the commands are still present in ESX) you shouldn’t as it might break ESX functionality (and is certainly not supported).
Firewall logging
The firewall logfile can be found at /var/log/vmware/esxcfg-firewall.log. This is largely an audit file containing changes to the firewall rules, NOT a log of the packets being either allowed or disallowed. Unlike many firewalls there isn’t a live console where you can see this info although it is possible to enable logging of denied packets following advice in this VMware communities post (refers to VI3 but still works fine for vSphere). The ‘-v’ parameter is undocumented although not sure why – seeing denied packets seems like useful functionality to me!
Further Reading/study
vSphere Command?Line Interface Installation and Scripting Guide
vSphere 4.0 Security Hardening Guide
vSphere 4.1 Hardening Guide (still in draft at time of writing, Feb 2011)

One thought on “VCAP-DCA Study notes 7.2– Configure and Maintain the ESX Firewall”