Summary: Some WordPress features can be abused and are therefore locked down by hosting companies. My hosting company recently made changes to their security which broke features I use for my blog. The fix, once identified, was quick and easy.
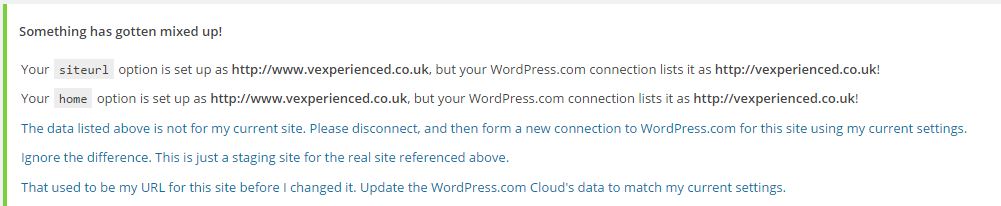
I’ve been blogging for around five years and am impressed with how easy and reliable WordPress has been over that time, despite constant updates. Earlier this week however I logged into my WordPress console and was greeted by an innocuous looking error message;
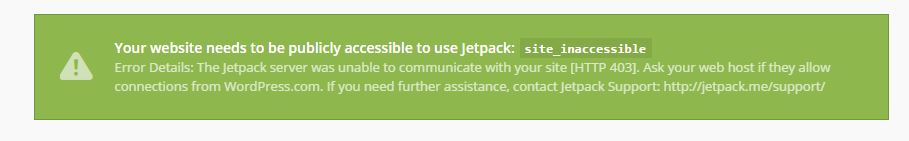
As suggested I tried disconnecting Jetpack and reconnecting but that didn’t work – Jetpack refused to reconnect and gave an error message saying my site wasn’t publicly accessible;
I tested the site which seemed to be available and working as expected. Diving a bit deeper I read into the plugin connectivity requirements and found that Jetpack (among others) relies on the XML-RPC protocol, which is now enabled by default in WordPress since v3.5. At a basic level you can test this by putting a simple URL in a browser – http://yourWordpressSite/xmlrpc.php – and it’ll return the single line ‘XML-RPC server accepts POST requests only‘. This worked fine for me but knowing that the mobile (iOS and Android) WordPress app used XML-RPC I tried those and found they weren’t working. Hmm.
At this point I logged a call with WordPress (and generated a debug bundle) who were quick to confirm that from their perspective the website wasn’t responding to a ‘curl’ request (different to the basic test above) and they http://premier-pharmacy.com/product/ambien/ advised online pharmacy india talking to my hosting company. I’d recently upgraded WordPress to v4.2 so suspected that might be related and in my opinion it seemed unlikely that the hosting company had locked down such a popular feature, certainly without notification, but I logged a call with them just to be sure. I was wrong and WordPress support were right! My hosting company (EvoHosting, highly recommended) advised me that due to DDoS attacks using aspects of the XML-RPC functionality they’d been forced to restrict it.
The fix was to install an additional WordPress plugin which limits the XML-RPC functionality (it stops XML-RPC pingbacks) but still allows the more popular features typically used by mobile WordPress apps and some plugins like Jetpack. With this installed they were able to whitelist my site and I was able to reconnect Jetpack and get my mobile apps working again. Obviously this fix won’t work for everyone as it depends on how restrictive your hosting company are – they may block XML-RPC completely, in which case you’ll have to plead your case. WordPress have a list of recommended hosting companies who all allow allow this functionality.
NOTE: I also believe this was the root cause of my the Jetpack Publicize issue whereby LinkedIn ‘needed refreshing’ constantly. Two birds with one stone…
Morale of the story – just because you work in IT don’t assume you know more than support teams. Some of them are very good and know their stuff! Guilty. 🙂