Knowledge
- Explain relationship between vDS and logical vSSes
Skills and Abilities
- Understand the use of command line tools to configure appropriate vDS settings on an ESX/ESXi host
- Determine use cases for and apply Port Binding settings
- Configure Live Port Moving
- Given a set of network requirements, identify the appropriate distributed switch technology to use
- Use command line tools to troubleshoot and identify configuration items from an existing vDS
Tools & learning resources
- Product Documentation
- ESX Configuration Guide
- ESXi Configuration Guide
- vSphere Command?Line Interface Installation and Scripting Guide
- vSphere Client
- vSphere CLI
- vicfg-*
- TA2525 – vSphere Networking Deep Dive (VMworld 2009 – free access)
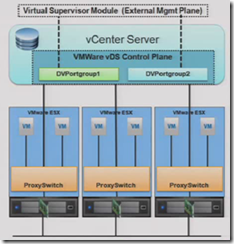
Relationship between vSS and vDS
Both standard (vSS) and distributed (vDS) switches can exist at the same time – indeed there’s good reason to use this ‘hybrid’ mode.
You can view the switch configuration on a host (both vSS and dvS) using esxcfg-vswitch -l. It won’t show the ‘hidden’ switches used under the hood by the vDS although you can read more about those in this useful article at RTFM or at Geeksilver’s blog.
Command line configuration of a vDS
The command line is pretty limited when it comes to vDS. Useful commands;
- esxcfg-vswitch
- esxcfg-vswitch -P vmnic0 -V 101 <dvSwitch> (link a physical NIC to a vDS)
- esxcfg-vswitch -Q vmnic0 -V 101 <dvSwitch> (unlink a physical NIC from a vDS)
- esxcfg-vswif -l | -d (list or delete a service console)
- esxcfg-nics
- net-dvs
NOTE: net-dvs can be used for diagnostics although it’s an unsupported command. It’s located in /usr/lib/vmware/bin. Use of this command is covered in section 6.4 Troubleshooting Network connectivity.
NOTE: esxcfg-vswitch can ONLY be used to link and unlink physical adaptors from a vDS. Use this to fix faulty network configurations. If necessary create a vSS switch and move your physical uplinks across to get your host back on the network. See VMwareKB1008127 or this blogpost for details.
Identify configuration items from an existing vDS
You can use esxcfg-vswitch -l to show the dvPort assigned to a given pNIC and dvPortGroup.
See the Troubleshooting Network connectivity section for more details.